New Questions on Png To Ico File Answered And Why You will Need to Rea…
페이지 정보
작성자 Alejandrina 댓글 0건 조회 11회 작성일 25-02-16 04:18본문
Since its inception, the Deobfuscator has proven to scale back analysis tasks that beforehand took days into ones that take mere minutes. The Deobfuscator can resolve: many forms of anti-disassembly corresponding to soar chains, push-returns, call-returns, return folds, bounce indirects, jumps into directions; several varieties of transfer and stack manipulation obfuscations, which attempt to mask the move of data; and unnecessary operations having no web impact. Guest Helikaon injects a bounce at runtime from kernel land into a user mode operating process quite than using commonplace debugger breakpoints like "INT 3" or DR0-DR7 hardware registers. This ultimate phase is about using IDA's graphical view to simplify the unpacking process and the way to make use of plugins and scripts to further shorten the unpacking time. Finally, we sum up all the partial products to obtain the ultimate end result. Avoid Merge Commits: Unlike merge, which can consequence in many merge commits, rebase keeps the history cleaner and linear. Because we’re the most effective and most affordable Similarweb alternate options, you can ever find on the internet. Alexander is without doubt one of the organizers of the Pwnie Awards. Alexander Sotirov has been involved in computer security since 1998, when he started contributing to Phreedom Magazine, a Bulgarian underground technical publication.
 Within the last 15 years Gerardo 'gera' Richarte has been dedicated to pc safety. Nicolas Pouvesle is a security researcher at Tenable Network Security the place he works on vulnerability analysis and reverse engineering. Nowadays, security research and vulnerability evaluation is becoming more particular and attacks tends to be software-centered. Aaron Portnoy is a researcher within TippingPoint's safety research group. Ali Rizvi-Santiago is a researcher within TippingPoint's security analysis group. Craig Smith is a Senior Application Security Consultant at Neohapsis. Craig makes a speciality of reverse engineering instruments and techniques with emphasis on malware and safety schemes. He is inquisitive about reverse engineering, vulnerability research and safety design. For the previous ten years he has been engaged on advanced exploitation, reverse engineering and vulnerability analysis. Developing C compilers for five years prior to reverse engineering has supplied a very good basis for understanding machine language and hardware to be utilized in reverse engineering duties. The market share for Apple units has grown significantly over the past few years, however most reverse engineering topics still deal with Microsoft platforms.
Within the last 15 years Gerardo 'gera' Richarte has been dedicated to pc safety. Nicolas Pouvesle is a security researcher at Tenable Network Security the place he works on vulnerability analysis and reverse engineering. Nowadays, security research and vulnerability evaluation is becoming more particular and attacks tends to be software-centered. Aaron Portnoy is a researcher within TippingPoint's safety research group. Ali Rizvi-Santiago is a researcher within TippingPoint's security analysis group. Craig Smith is a Senior Application Security Consultant at Neohapsis. Craig makes a speciality of reverse engineering instruments and techniques with emphasis on malware and safety schemes. He is inquisitive about reverse engineering, vulnerability research and safety design. For the previous ten years he has been engaged on advanced exploitation, reverse engineering and vulnerability analysis. Developing C compilers for five years prior to reverse engineering has supplied a very good basis for understanding machine language and hardware to be utilized in reverse engineering duties. The market share for Apple units has grown significantly over the past few years, however most reverse engineering topics still deal with Microsoft platforms.
Although loads of research has been performed into exploiting remote buffer overflows in kernel mode on modern systems like Windows, Linux and BSD, there are actually few publications about exploitation on other platforms that are nonetheless common in enterprise networks. On this chapter, allow us to talk about about the essential arithmetic circuits like Binary adder and Binary subtractor. Rounding. PayPal charges are rounded using arithmetic rounding. Listed here are some tips that you should use to extend it. Here is the place you start placing every little thing together. Your first step should be to start out tracking da checker moz, then engaged on methods to drive your number up. By default, the quantity is constructive, prefix a sprint (-) symbol for a adverse number. He has written customized instruments for Immunity shoppers in addition to several binary evaluation seo studio tools youtube for the Immunity Debugger. It's possible you'll obtain pricing info for supplemental companies or options, in addition to solutions to frequent billing questions by going to the NetZero Site.
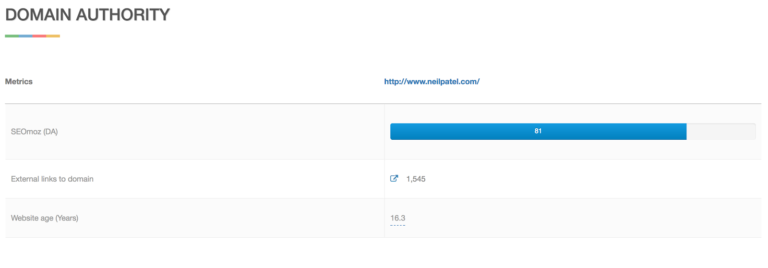
The second instrument may be helpful when reversing from binary back to C code. It's vital to note that Paypal may update its price construction now and again, so it's recommended to check the latest fee information on the Paypal website or seek the advice of their official documentation for the latest charge percentages and particulars. During newest year, seo tools he discovered many vulnerabilities which have resulted in several Microsoft bulletins. Aaron has found critical vulnerabilities affecting a wide range of enterprise vendors including: Microsoft, RSA, Adobe, Citrix, Symantec, Hewlett-Packard, IBM and others. Additionally, Aaron has spoken at BlackHat US, BlackHat Japan, Microsoft BlueHat, Toorcon Seattle, and DeepSec. Understanding these gaps helps prioritize improvements that could have the most vital impact on your domain authority. Valuable and promotable website content shouldn't be only critical to getting your account permitted, but it also ensures that the Google Ad Grant really helps you achieve meaningful conversions. Enhance Website Speed: Improve your site’s loading pace utilizing strategies reminiscent of image optimization, leveraging browser caching, and minimizing HTTP requests. Image Prospector features a free tier for tracking 10 images and three paid plans.
When you loved this informative article in addition to you desire to be given more info relating to png to ico file (https://telegra.ph/SEO-Studio-Tools-The-Complete-Solution-for-Effective-SEO-Strategy-02-11) kindly check out our own web page.
댓글목록
등록된 댓글이 없습니다.